Background
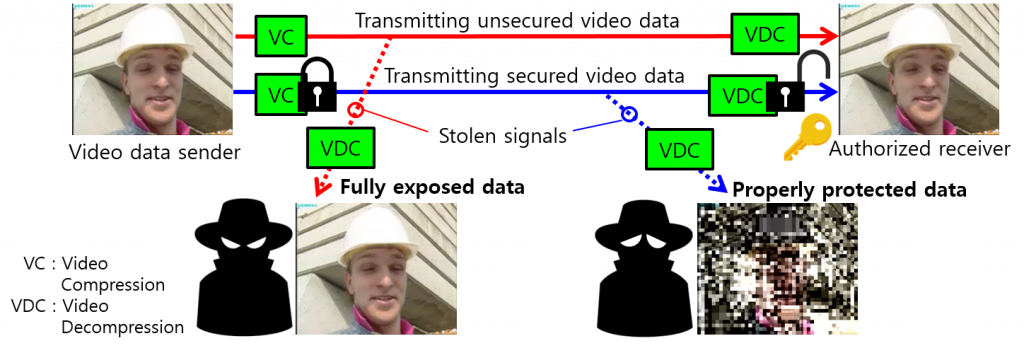
Thanks to the technology advances, embedded systems have been widely used in everywhere. In those embedded systems such as smartphones and wearable devices, image and video sensors are utilized to provide various services. Accordingly, many kinds of video applications have been developed. Some of those applications provide entertainments but some other applications deal with privacy-critical and security-critical video data. For example, private video chat between individuals expose their privacy such as private room. Video conferencing has been widely used in business and governmental meeting. In this case, video data could include critical and financial information. In addition, video applications used in military could process extremely classified video data. Video applications used in telemedicine include patient’s privacy and life-critical video information. Therefore, many people concern about privacy and security of important video data in various video applications.
Protect important video data
According to the concerns about privacy and security of important video data, protection techniques to protect those data have been designed. Traditional text encryption algorithms such as DES (Data Encryption Standard) and AES (Advanced Encryption Standard) can be utilized to protect video data. Moreover, various video encryption techniques which consider the characteristics of video data have been proposed. Encryption techniques can be applied before and after the video compression process. Otherwise, techniques could be embedded into the video compression process. Moreover, some techniques protect the entire video data while some other techniques encrypt just several parts of the whole data.
Evaluate visual security of encrypted videos
In case of text encryption, the number of attacks to break the algorithm is used to represent the encryption power of the algorithm in general. However, in case of video encryption, we should consider one more thing, that is visual security of encrypted videos. Visual security represents how much visually distorted when we see the encrypted videos. We can say “the encrypted video A is more visually distorted than the encrypted video B” or “the encrypted video A is heavily distorted while the encrypted video B slightly exposes the frames of the objects”. However, such representations of visual security cannot be used to compare the encryption power of encryption algorithms because each individual have his own criteria for the visual distortion and that is definitely subject, not object. Therefore, we need to represent the visual security of encrypted videos in the objective manner such as numbered levels. PSNR (Peak Signal-to-Noise Ratio) and SSIM (Structural Similarity) have been widely used to represent visual quality of videos. Moreover, several visual security metrics have been proposed to estimate visual security of encrypted videos.
Energy consumption of video applications with protection techniques
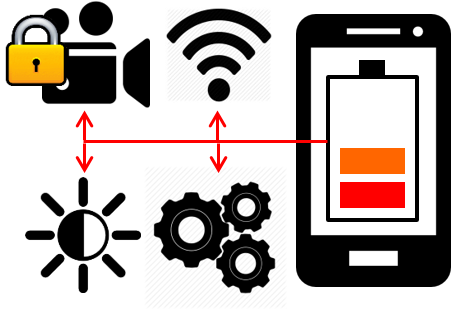
Video coding, which includes video encoding(=compression) and video decoding(=decompression), consumes huge energy due to lots of computations. In addition, video encryption/decryption add more computational overheads, thereby consuming more energy. However, we have limited power resources because mobile devices have limited battery capacity. Moreover, there are several applications and background jobs in mobile devices. Therefore, we should efficiently perform video applications with protection techniques under given energy budget.
Relevant Publications
- Junhyung Moon, Hwisoo So, Kyoungwoo Lee, “Configurable privacy management for secure video surveillance in energy-constrained systems”, IEEE International Conference on Systems, Man, and Cybernetics, Oct, 2016.
- Junhyung Moon, Kyoungwoo Lee, “Integrated visual security management for video encryption in limited battery devices”, IEEE Symposium on Embedded Systems For Real-time Multimedia, Oct, 2015.
- Junhyung Moon, Kyoungwoo Lee, “Spatio-temporal visual security metric for secure mobile video applications”, ACM International Workshop on Mobile Video, Mar, 2015.
- 김형준, 문준형, 김현충, 이경우, “H.264에서의 정적 영상 보안을 위한 움직임 벡터의 효율적인 암호화 기법”, 한국정보과학회 한국컴퓨터종합학술대회, May, 2014.
- 이주성, 문준형, 김수환, 박희민, 이경우, “모바일 보안 영상통신에서의 성능과 에너지 소모량, 화질간의 연관성 분석”, 정보과학회논문지, May, 2013.
- 이주성, 문준형, 김수환, 박희민, 이경우, “모바일 기기에서 보안 영상 통신의 영상 품질, 성능과 에너지 소모의 연관성에 대한 실증 연구”, 한국정보과학회 추계학술발표회, Oct, 2012.